WordPress Plugin Flaw Puts 90K+ Websites at Risk: Over 90,000 websites face a serious threat due to a recently discovered vulnerability in the WordPress Backup Migration Plugin, exposing them to potential hack attacks.

Discovery by Nex Team in Wordfence Bug Bounty Program
Researchers from Nex Team identified the critical vulnerability, marked as CVE-2023-6553, during their participation in the Wordfence Bug Bounty program.
Severity Score: Critical 9.8
The CVE-2023-6553 vulnerability, allowing unauthenticated remote code execution, has been assigned a high severity score of 9.8, posing a significant risk to the affected websites.
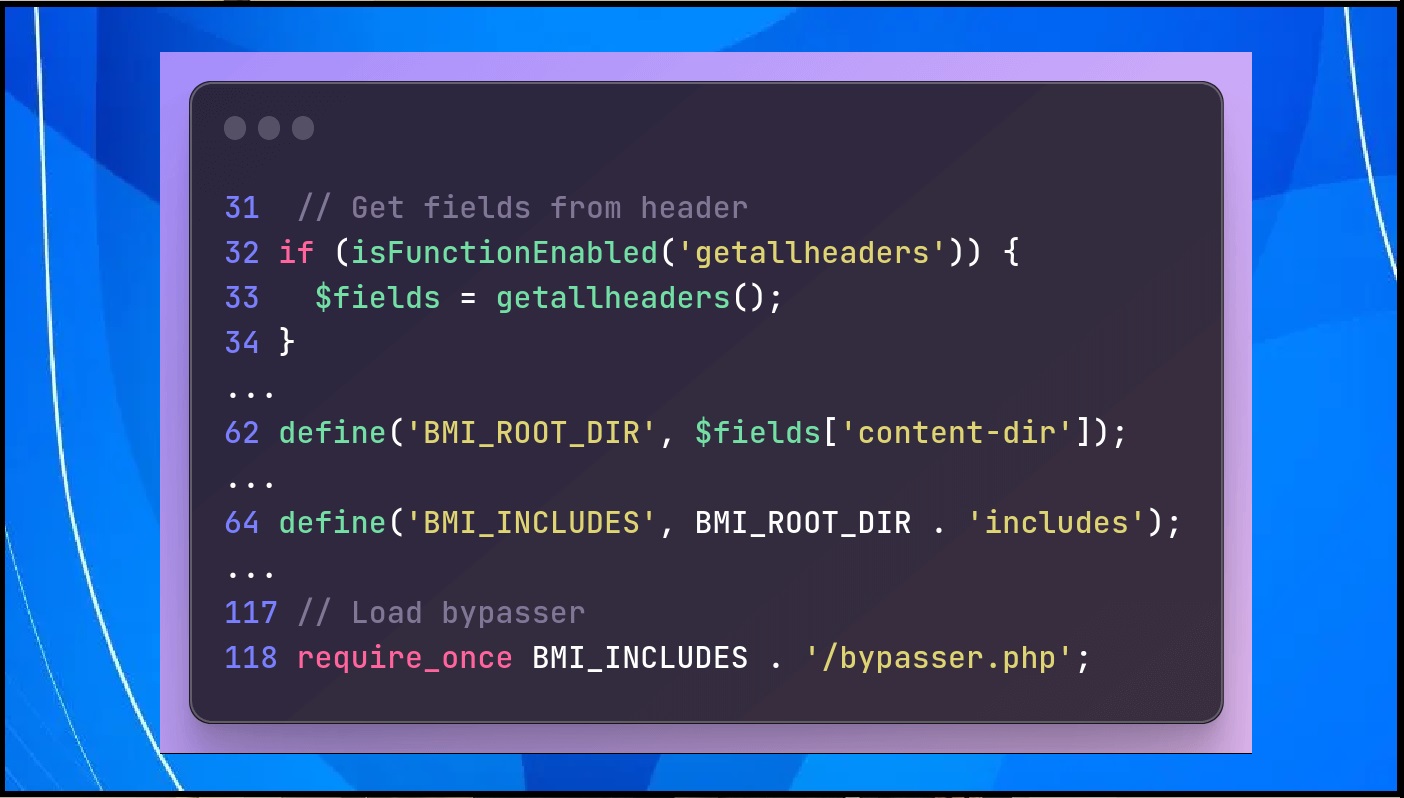
Unauthenticated Remote Code Execution Exploitation
The vulnerability enables unauthenticated threat actors to execute arbitrary PHP code on WordPress sites using the Backup Migration Plugin. This opens the door for attackers to gain unauthorized access and potentially compromise sensitive data.
Specifics of the Vulnerability
The flaw is present in all versions of the Backup Migration plugin up to and including 1.3.7, residing in the /includes/backup-heart.php file. Exploiting this weakness allows attackers to execute remote code, posing a serious security threat.
Remote Code Execution (RCE) Explained
In the context of this vulnerability, Remote Code Execution (RCE) refers to the ability of threat actors to inject and execute arbitrary PHP code on a target WordPress site, potentially compromising its security.
Exploitation Process and Potential Risks
If an attacker gains control of a target computer through an unrelated vulnerability, they can exploit this WordPress plugin flaw to insert malicious PHP code, running arbitrary commands on the underlying server within the WordPress instance’s security context.
Immediate Action Required: Update to Version 1.3.8
In response to the vulnerability, the plugin’s developers swiftly released version 1.3.8, including a patch to address the identified issue. Website administrators are strongly advised to update the plugin to the latest version promptly to prevent the exploitation of this critical vulnerability.
In Conclusion, Safeguarding Websites As the security landscape evolves, staying vigilant and promptly addressing vulnerabilities is crucial. Keeping plugins up-to-date ensures a more secure online environment, protecting websites and their users from potential threats.

